DevSecOps for $0
Building a Free, Enterprise-Grade DevSecOps Pipeline Using GitHub Actions (Step-by-Step)
Most companies rely on expensive security platforms to secure their CI/CD pipelines.
I wanted to challenge that idea.
So I spent a few days building a complete, multi-layer DevSecOps pipeline using:
GitHub Actions Free Tier
100% open-source security tools
A small Python web app + Dockerfile
Terraform IaC configs
My goal was simple:
How close can I get to enterprise-grade automation with zero licensing cost?
Spoiler: surprisingly close.
A Simple Analogy Before We Dive In
Think about how airports secure every passenger:
Security check → ID verification → Baggage scan → Body scan → Random screening → Gate clearance → Final scan.
Each step protects you from a different risk.
A modern application needs the same type of layered protection.
This pipeline recreates that idea, but for software.
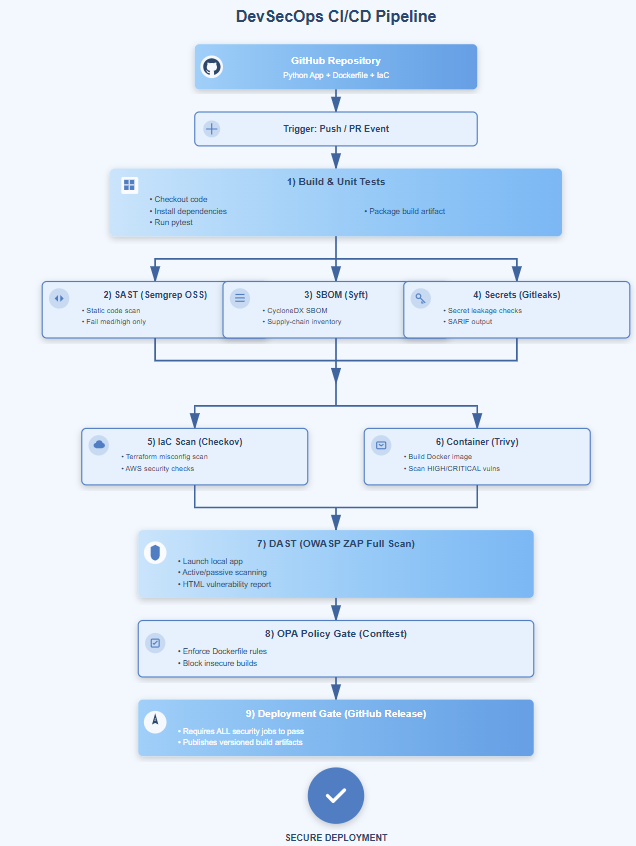
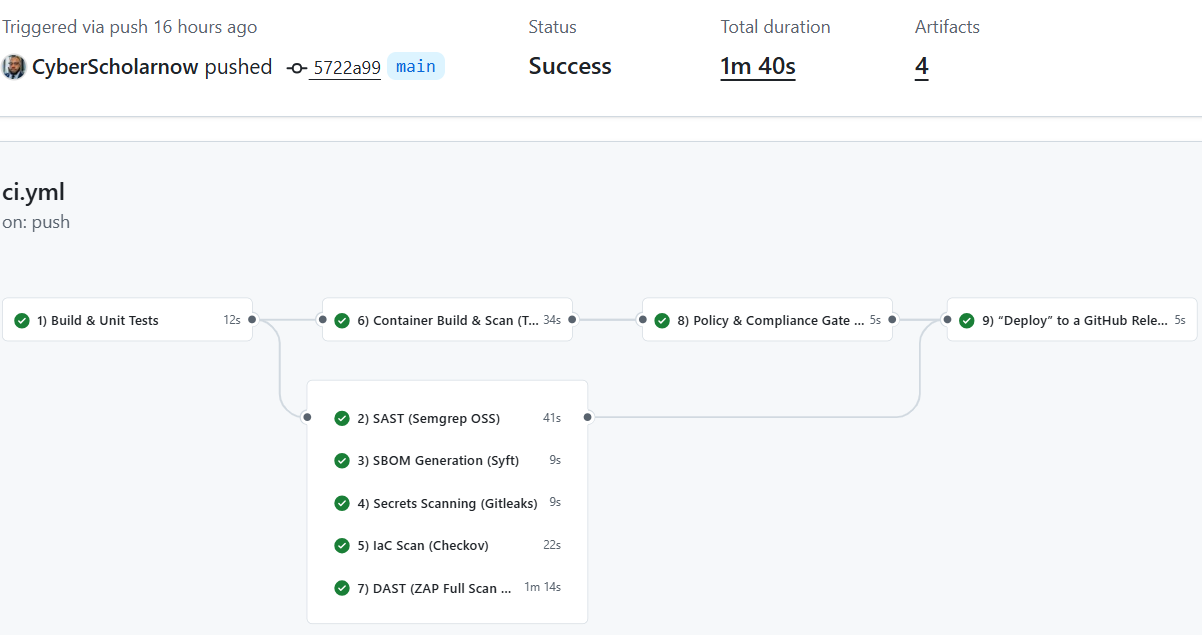
What This Pipeline Does (High-Level Overview)
Every time someone pushes or opens a pull request, the pipeline automatically performs nine security and quality checks, each targeting a different risk:
Unit Tests
Static code analysis (SAST)
Secrets scanning
SBOM generation
Infrastructure as Code scanning
Container vulnerability scan
Dynamic application testing (DAST)
Policy enforcement (OPA Gate)
Secure deployment (only if everything passes)
All completely automated.
All free.
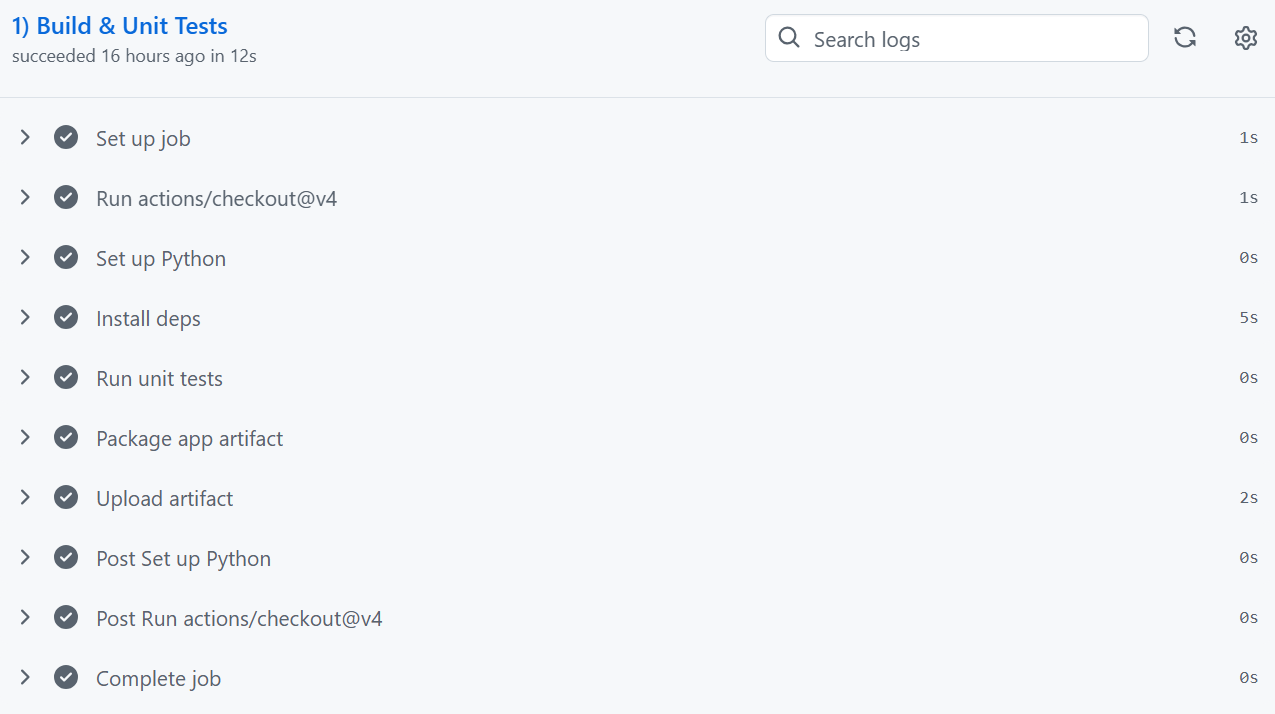
1. Build & Unit Tests (pytest)
This is the “does the engine even start?” stage.
The pipeline:
Installs dependencies
Runs unit tests
Packages the app into an artifact
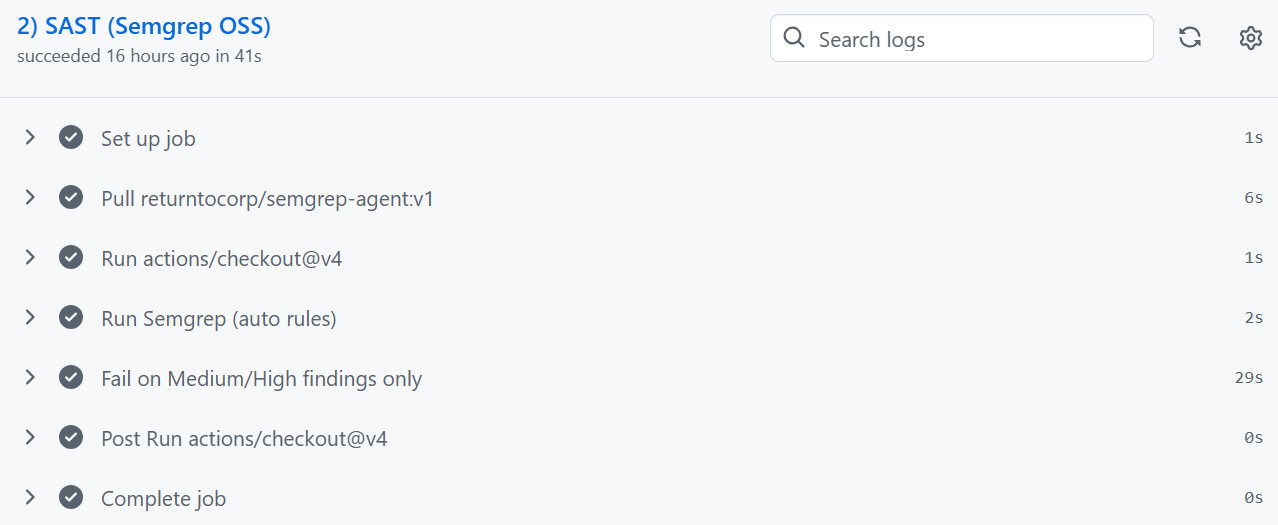
2. SAST With Semgrep
Static code scanning catches vulnerabilities before the code even runs.
Semgrep checks for:
Insecure patterns
Hardcoded secrets
Dangerous function usage
Common OWASP patterns
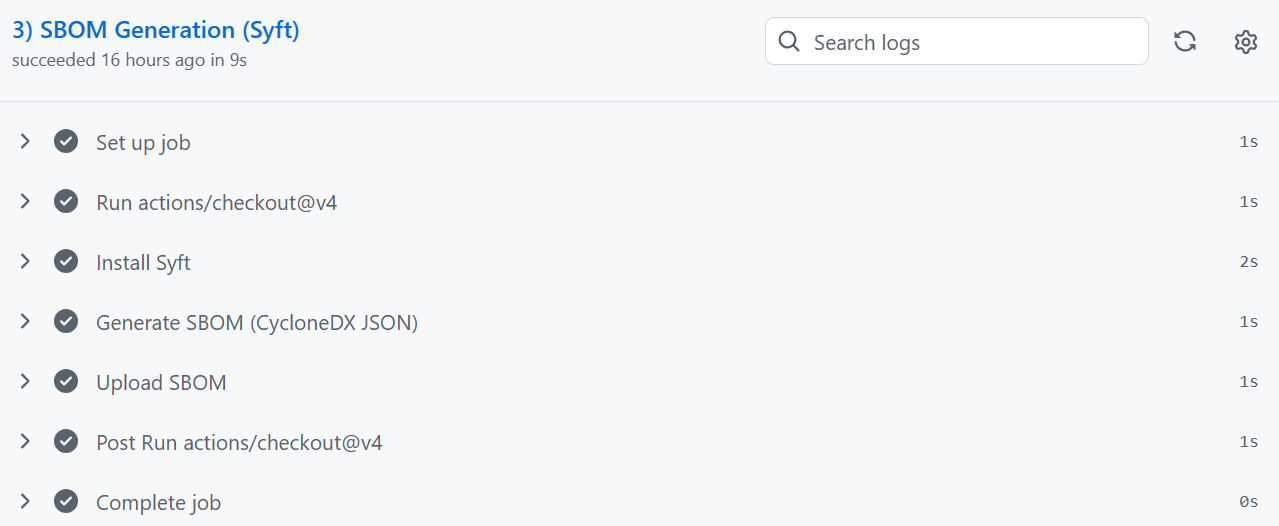
3. SBOM Generation With Syft (CycloneDX)
The pipeline creates a Software Bill of Materials, a complete inventory of:
Libraries
Dependencies
Versions
Metadata
This is required by modern supply-chain security standards.
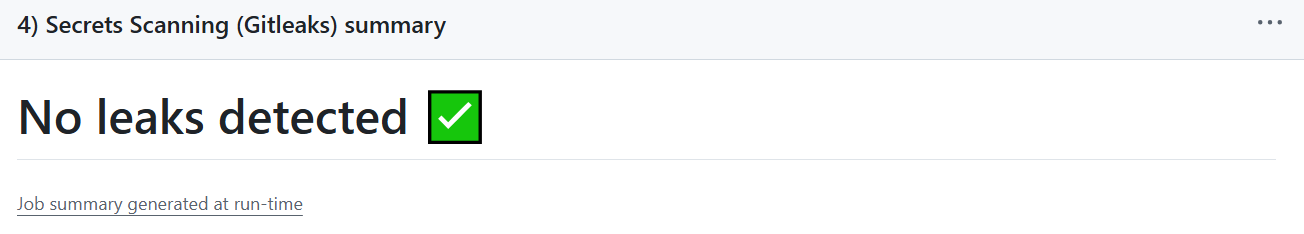
4. Secrets Scanning With Gitleaks
Gitleaks prevents API keys, credentials, and tokens from ever getting committed.
This protects both you and the organization using your code.
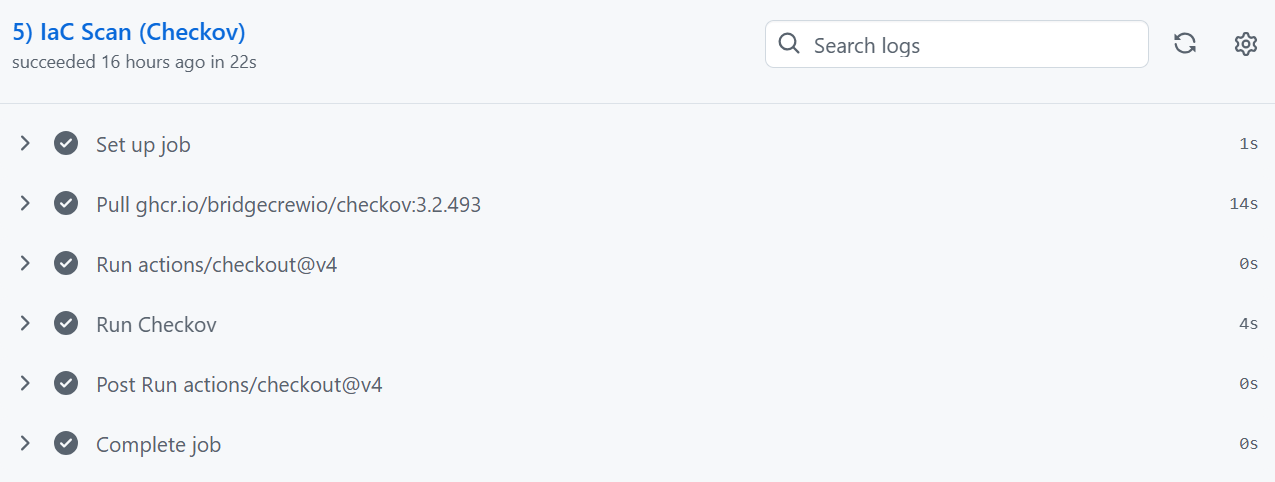
5. IaC Security Scanning With Checkov
Checkov reviews the Terraform files for:
AWS misconfigurations
Public S3 buckets
Missing encryption
IAM policy risks
Network exposure
IaC flaws are one of the biggest cloud breach risks this stops them early.
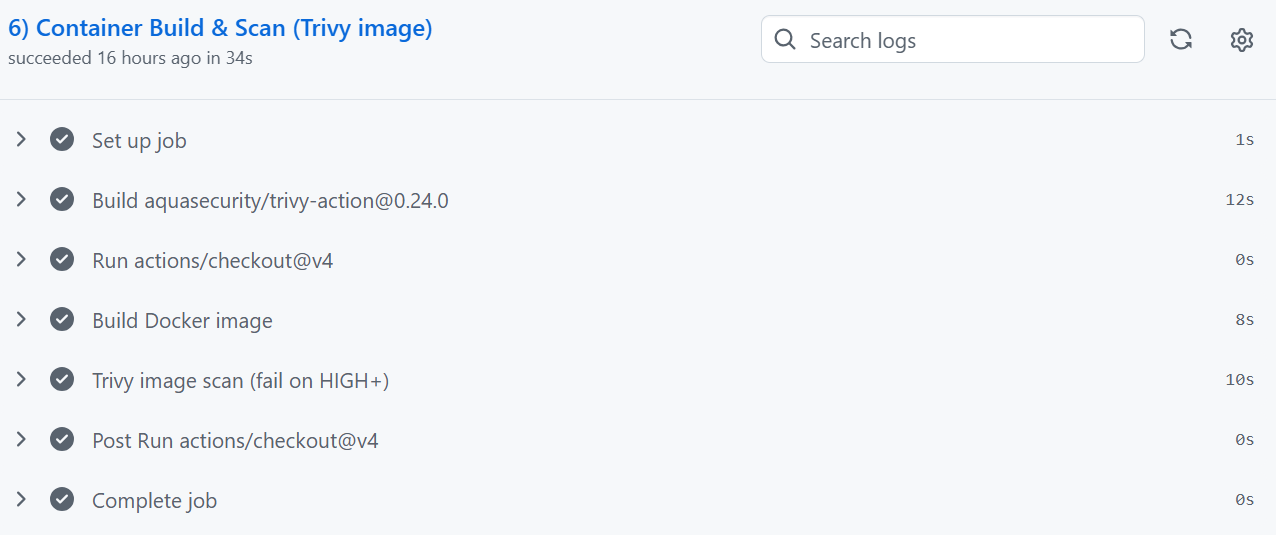
6. Container Scanning With Trivy
Trivy scans the built Docker image for HIGH/CRITICAL CVEs.
This ensures the app doesn’t deploy with known vulnerabilities in:
Base image layers
Python libraries
OS packages
7. DAST With OWASP ZAP (Docker Full Scan)
This is the “red team” stage.
ZAP actually launches your running app and performs:
Passive scanning
Active attacks
Alert detection
OWASP Top 10 checks
8. Policy Enforcement Using OPA + Conftest
This prevents unsafe Dockerfiles from being built.
You define security rules such as:
No root user
Must use non-latest tags
Must copy specific files
Must expose only expected ports
If a rule fails, the pipeline stops immediately.
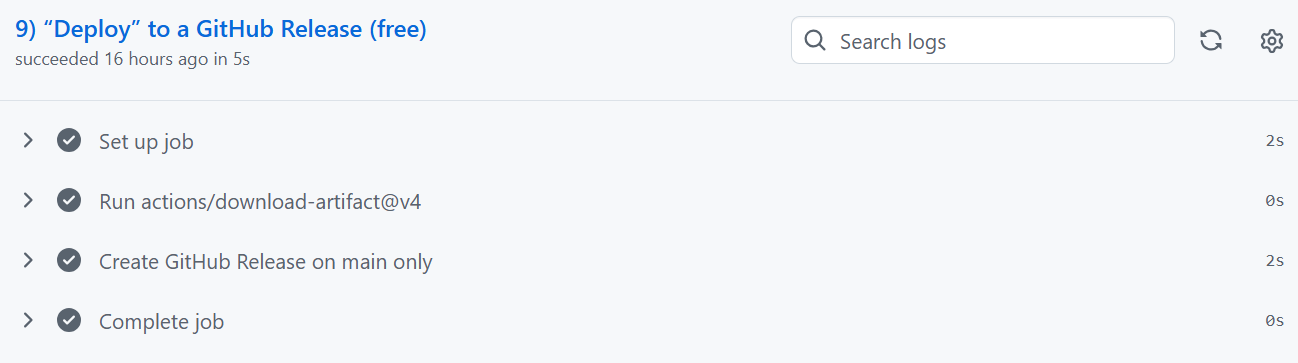
9. Deployment Gate GitHub Releases
Nothing is deployed unless every security layer turns green.
If everything passes:
GitHub automatically publishes a secure artifact release
It’s versioned
It’s immutable
It’s ready for distribution or deployment
Why This Matters
This project shows:
You understand the full SDLC, not just cloud security
You can build enterprise-grade automation using OSS tools
You know how to operationalize security, not just talk about it
You’ve implemented SAST + DAST + IaC + Containers + SBOM + Policy the full suite
You can design, codify, and enforce security as code
Want to Explore the Code?
https://github.com/CyberScholarnow/complete-devsecops-demo
Thank you for reading my blog post.